Advanced Cybersecurity Solutions to Defend Your Business Against the Most Complex Threats
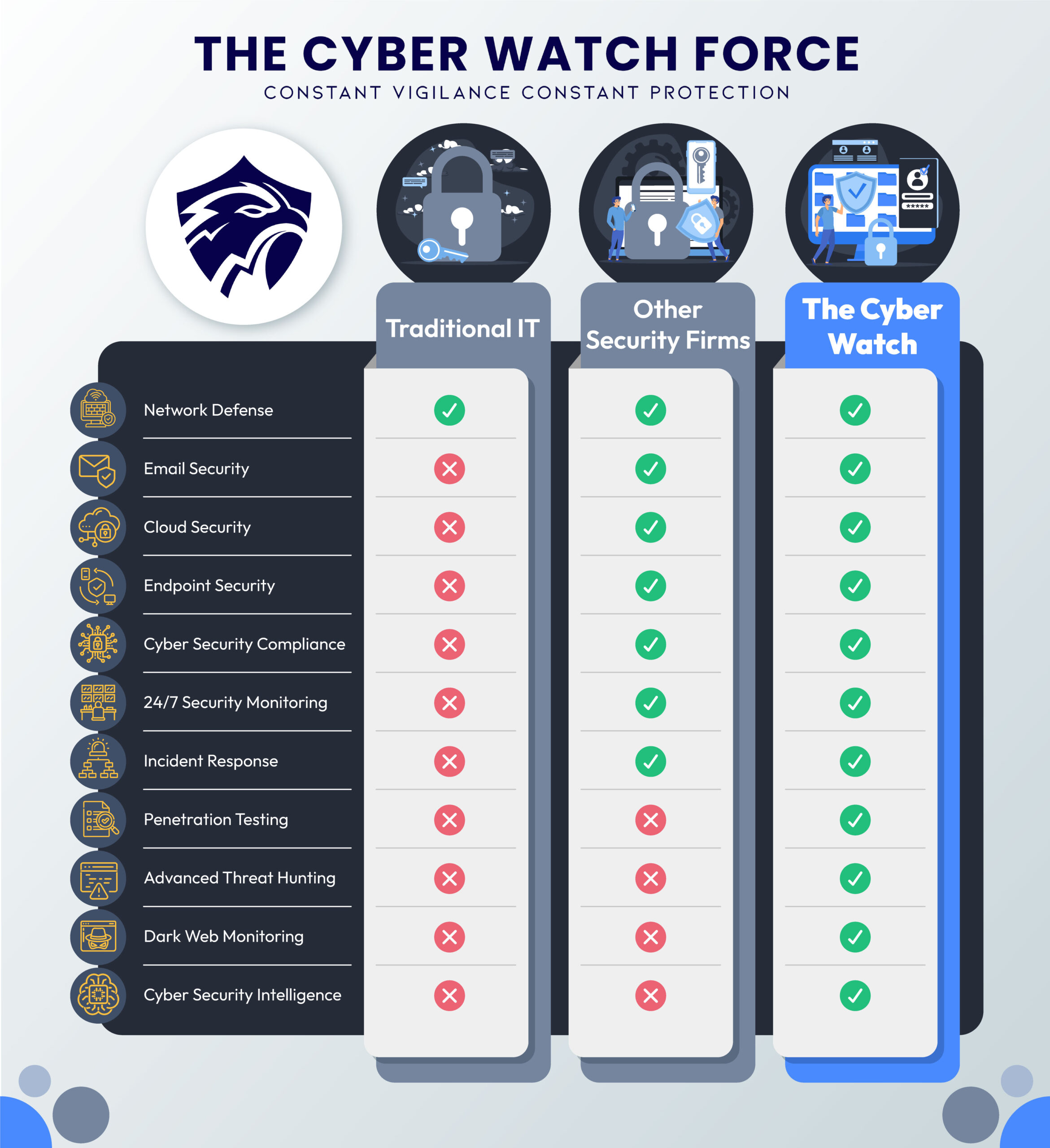
The Cyber Watch Force
Our Mission: Constant Vigilance Constant Protection
Don’t risk your business with outdated security measures or reactive solutions that are always a step behind. Choose The Cyber Watch Force as your proactive defense ally, dedicated to safeguarding your business. Our certified professionals leverage state-of-the-art technology and proven experience to build an unbreakable barrier around your digital assets.

How We Defend

Counter Adversary Operations
Our elite team is dedicated to continuously tracking the latest developments in cyber intelligence, attack frameworks, and dark web activity. By collecting vital information on emerging threats we maintain a continuous threat visibility that provides us with crucial insights into global adversaries and their activities. This capability allows us to swiftly detect, investigate, and thwart potential threats.

24/7 Security Monitoring
Our security monitoring operates around the clock, providing an essential layer of protection that is always vigilant, never faltering, and consistently alert to any potential threats. This continuous surveillance ensures that every corner of your environment is under scrutiny, allowing us to detect anomalies and suspicious activities in real-time.

Offensive Security
Our team conducts meticulous penetration testing to thoroughly identify and address any vulnerabilities within your systems before they can be exploited by malicious actors. This proactive approach not only helps in fortifying your defenses but also ensures that potential weaknesses are remediated in a timely manner.

Proactive Defense
In the ever-evolving realm of cybersecurity, merely reacting to threats is no longer enough. We understand this critical need and have embraced a proactive methodology. By actively monitoring the latest cyber intelligence, attack frameworks, and dark web insights, along with conducting thorough penetration testing and advanced threat hunting ensures we are always one step ahead of threats.
Know The Numbers
%
89% of organizations in the United States exprerienced at least one cyber attack in the last 12 months.
%
73% of American small business owners reported a cyber attack last year.
%
43% of organizations lost existing customers because of cyberattacks.
Ensure your business isn’t just another number in the alarming statistics of cyber attacks.
Proud To Protect These Industries

Safeguard the confidentiality of patient records (PHI) and guarantee adherence to HIPAA regulations.

Ensure the security of customer data (PII), prevent unauthorized system access, and achieve compliance with PCI-DSS requirements.

Shield your customers and their sensitive financial information (PII) from malicious actors.

Shield your students and staff’s data from malicious actors and guarantee that your computer systems are consistently protected.
Our Services:
We Provides Expert Cybersecurity Solutions Tailored To Protect Your Digital Assets

Endpoint Security
Protect your organization with the latest in endpoint security, designed to thwart everything from basic malware to complex fileless and zero-day threats. We use exceptional threat intelligence, enabling early detection and prevention of attacks through advanced script control and memory scanning techniques. By addressing malicious behaviors at the initial stages of the kill chain, you can fortify your defenses and maintain a secure environment.
Network Security
Protect and empower your business network with the integrated security solutions from The Cyberwatch Force. In an era where businesses demand seamless, layered security across all endpoints and users, no matter where they operate, The Cyberwatch Force stands ready to assist you in achieving that goal.


Email Security
Most targeted attacks initiate through email, exploiting the most vulnerable aspect of your security: people. Phishing and spear-phishing schemes remain alarmingly effective at stealing both money and sensitive information. Given that email serves as a goldmine of critical information and a direct channel for social engineering, cybercriminals are increasingly adept at altering file formats to bypass security measures and embedding harmful links within emails. Our dedicated team of security experts is well-versed in the various email-based attacks and consistently works to protect against these dangers
Cloud Security
Cloud applications offer remarkable flexibility and speed, allowing for rapid development and deployment. However, this agility comes with increased exposure to security threats. Industries like manufacturing, public services, healthcare, retail, education, and utilities often find their cloud applications susceptible to a range of vulnerabilities. We can establish tailored policies, processes, and controls designed to mitigate the risks associated with cloud-based applications, protecting them from both external and internal threats. Additionally, we provide continuous monitoring of your cloud resources to ensure they remain secure from potential attacks.


Penetration Testing
Cybercriminals, hackers, and automated bots, are relentlessly seeking vulnerabilities in your business and personal data. If they succeed, they can gain access to sensitive information and inflict lasting harm. To combat this threat, we can conduct penetration testing, allowing us to stay ahead of attackers and ensure your business remains secure at all times.
Cyber Security Auditing & Compliance
Our dedicated team of security audit specialists is committed to providing a meticulous and comprehensive Cyber Security Audit, Compliance Audit, and Data Security Audit. This thorough examination is designed to uncover any vulnerabilities and security gaps that may exist within your organization. By employing a systematic approach, we will not only identify these weaknesses but also analyze the contributing factors that lead to non-compliance with industry standards and regulations. Our goal is to equip your organization with the insights needed to enhance your security posture and ensure adherence to compliance requirements.

Our Certifications Include: