Dark Web Monitoring
The 2024 Global Threat Report by Crowdstrike Falcon reveals that an astonishing 75% of security breaches and intrusions occurred without the use of malware. Instead, attackers gained access to systems by utilizing stolen credentials purchased from the deep and dark web. This highlights the adage that logging in is often easier than hacking in.
%
75% Of Intrusions And Breaches Were Carried Out Without Malware

What Is The Dark Web?
The dark web represents a concealed part of the internet that is not accessible through standard search engines found on the surface web. To navigate this hidden realm, users must utilize a specialized anonymous browser known as Tor. Tor offers enhanced privacy features, making it particularly appealing to individuals such as threat actors, cybercriminals, hackers, and government agents who seek to maintain their anonymity.
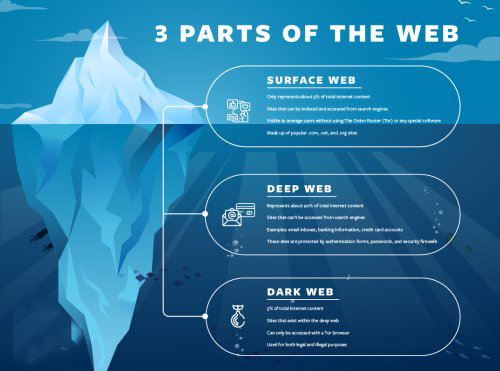
Open Web vs. Dark Web vs. Deep Web: What’s the Difference?

Open Web
The Open Web, often referred to as the surface web, represents the most easily accessible segment of the internet, which can be effortlessly explored using well-known search engines such as Firefox, Google, Bing, and Yahoo. This layer includes publicly available domains like websites, social media networks, news outlets, and e-commerce platforms—content that is reachable by anyone with internet access and a web browser.
Deep Web
The Deep Web represents a vast and concealed layer of the internet that is inaccessible to standard search engines. This area includes content that necessitates particular permissions, login information, or specialized tools for entry. Examples of this include websites secured by passwords, private databases, and subscription-only resources, all of which contribute to a larger, albeit less apparent, segment of the online world.

Dark Web
The Dark Web is a hidden segment of the Deep Web that requires specialized tools, like the Tor browser, for access. This area features anonymous websites, forums, and marketplaces that emphasize user privacy and confidentiality. It is important to recognize that, although the Dark Web can have legitimate uses, it is frequently linked to illegal activities, attracting individuals such as cybercriminals, hackers, and threat actors.
Why We Monitoring The Dark Web
Our team actively monitors the Dark Web to protect your organization’s sensitive information. We employ specialized Dark Web monitoring tools that function similarly to search engines, allowing us to detect leaked or stolen data such as compromised passwords, breached credentials, and intellectual property. Furthermore, we track discussions of potential cyber threats targeting your organization among malicious actors operating in this hidden part of the internet.


How We Are Monitoring The Dark Web
Our Dark Web monitoring involves continuous searches that yield real-time raw intelligence. We scrutinize millions of websites to extract targeted information, such as corporate email addresses, as well as general details like your company name and industry. Upon detecting a threat, we immediately inform your employees and any pertinent teams within your organization, including marketing, legal, human resources, and fraud departments. This ensures that your systems remain secure and protected from potential breaches.
Why We Monitoring The Dark Web
Our team actively monitors the Dark Web to protect your organization’s sensitive information. We employ specialized Dark Web monitoring tools that function similarly to search engines, allowing us to detect leaked or stolen data such as compromised passwords, breached credentials, and intellectual property. Furthermore, we track discussions of potential cyber threats targeting your organization among malicious actors operating in this hidden part of the internet.

How Dark Web Monitoring Can Benefit Your Organization
A Strategic Security Insights
Data collected from the dark web can reveal important insights into potential threats and intelligence, helping to identify possible cyber attacks against your organization and supporting effective strategic risk management.
Prevention Of Data Breaches
Keeping an eye on the dark web allows us to identify if your sensitive information has been exposed. This proactive approach is essential for stopping more significant data breaches before they occur.
Protection Of Intellectual Property
Companies invest significant time in creating products, and services, and building their brand image. Unfortunately, the dark web serves as a platform for the illicit trade of stolen intellectual property, trade secrets, and sensitive information. Are Monitoring empowers businesses to identify any unauthorized sharing or selling of their proprietary data.


